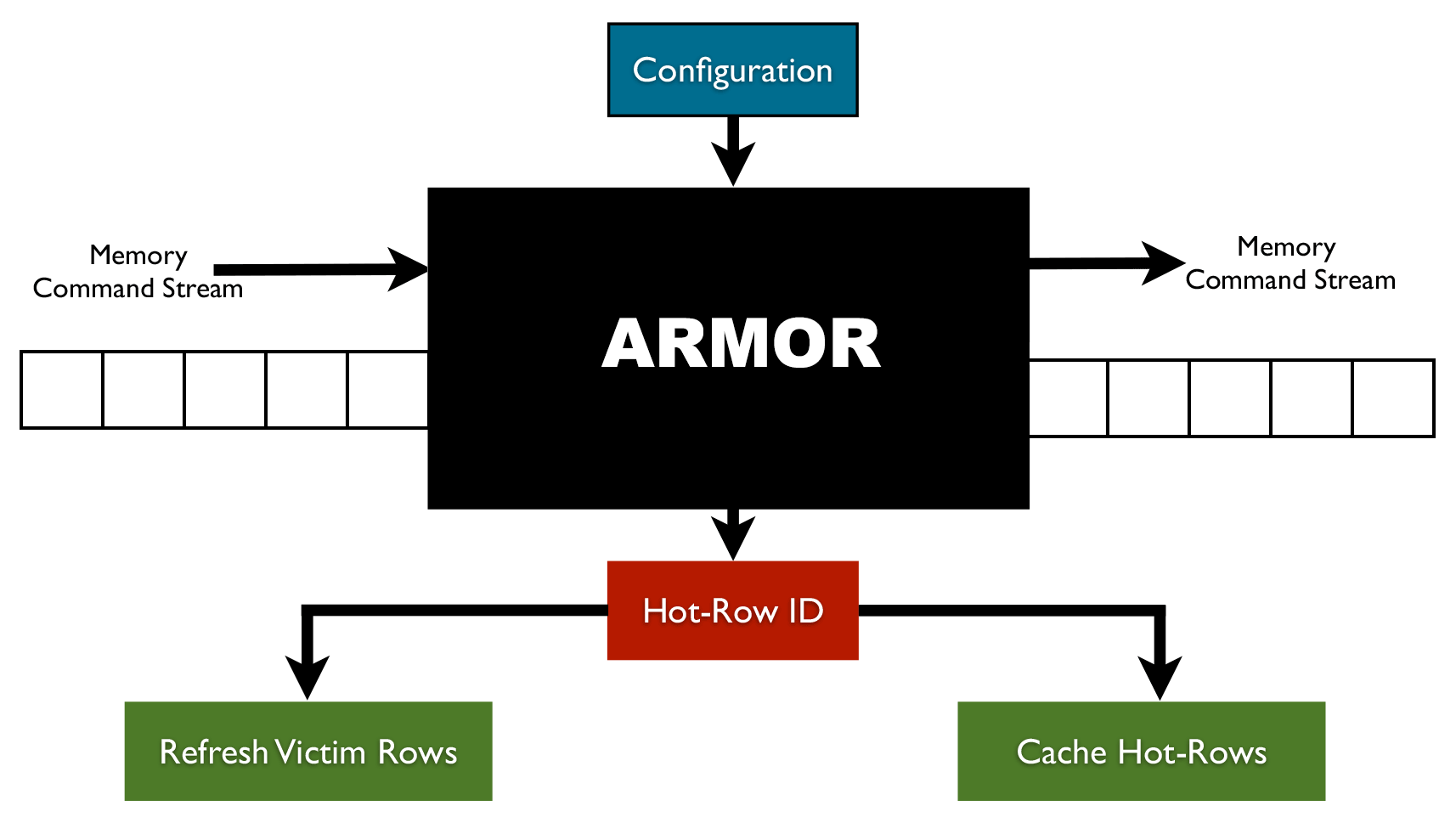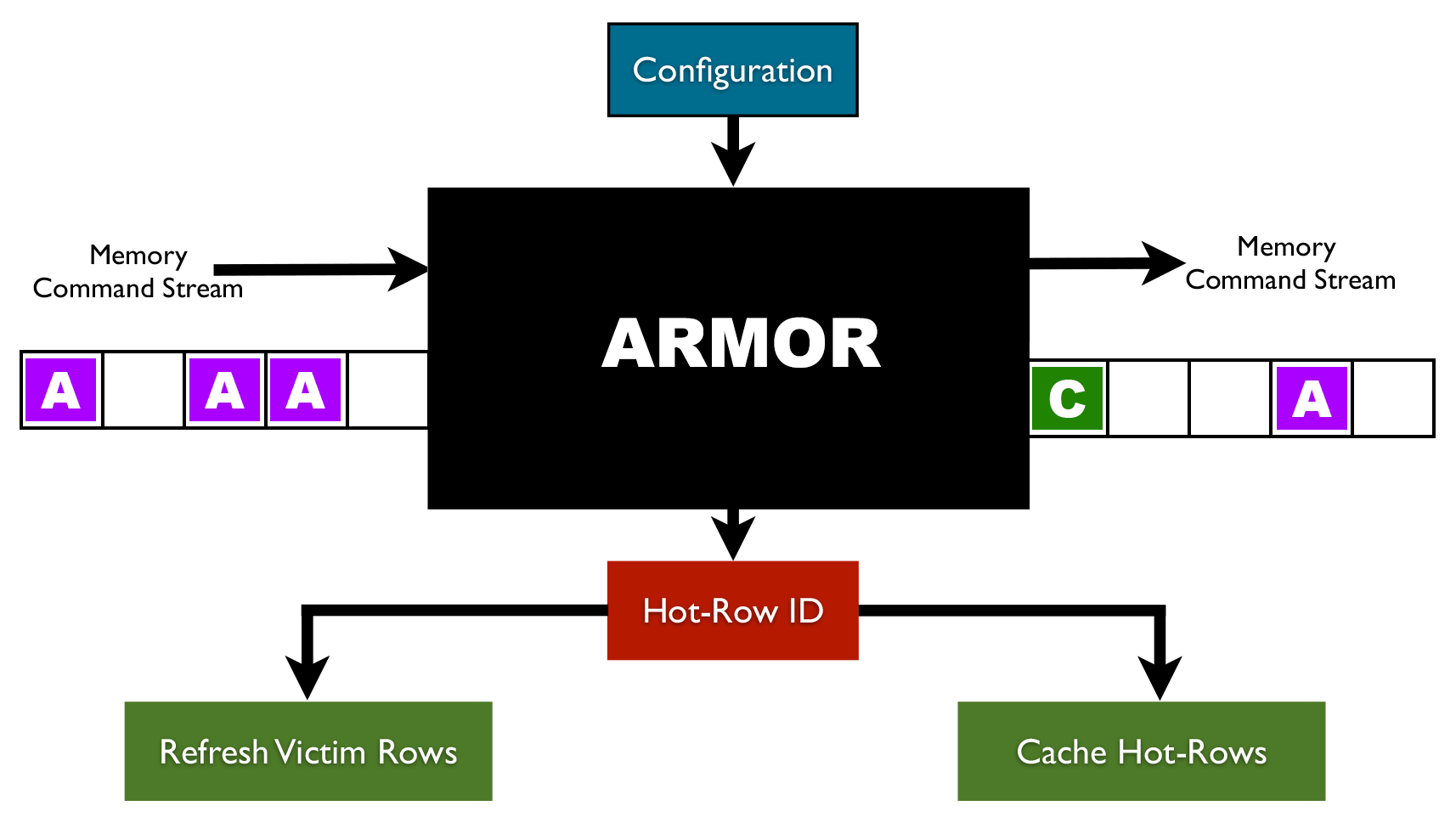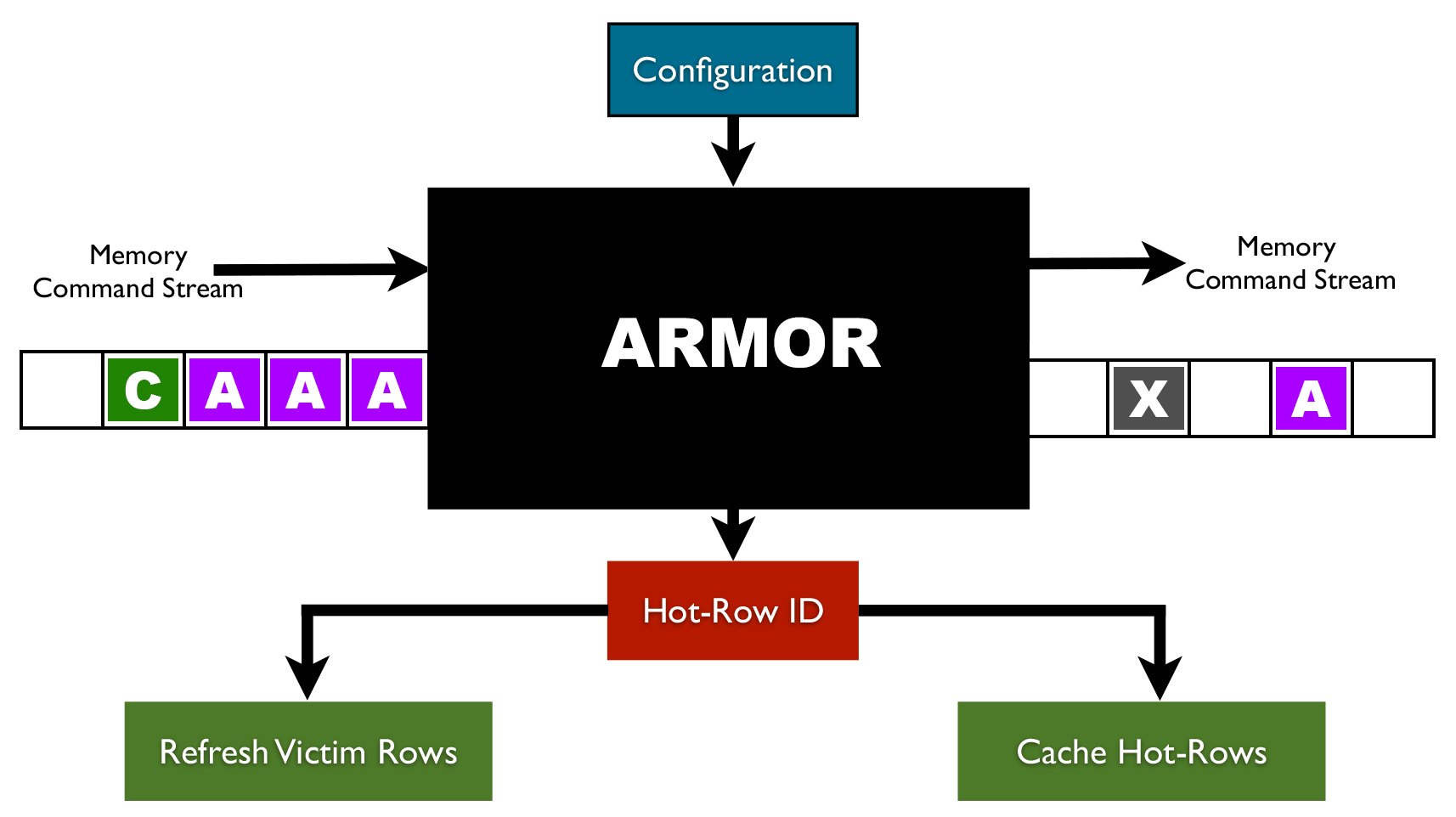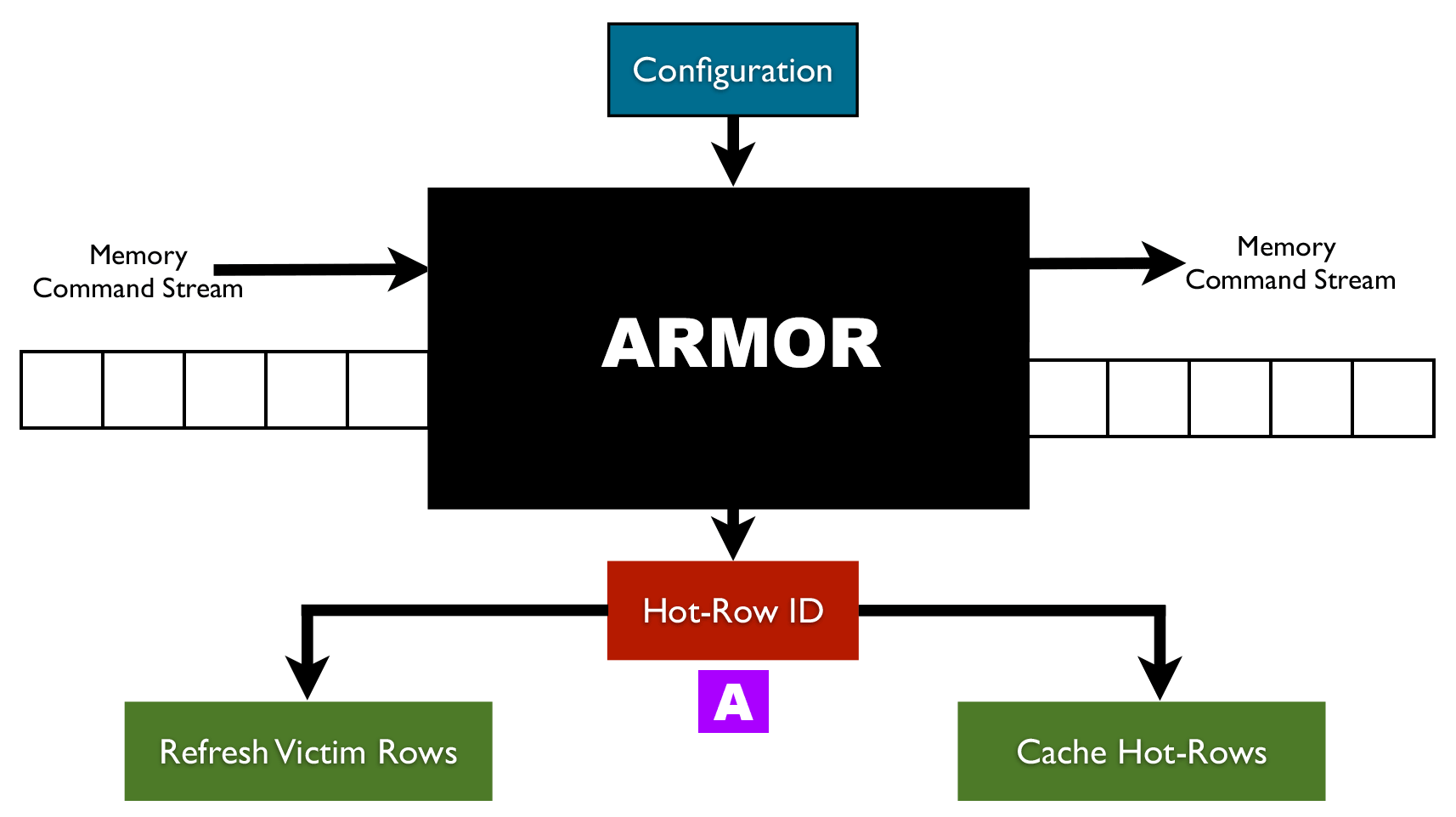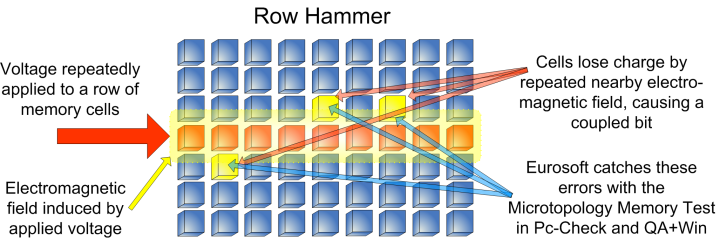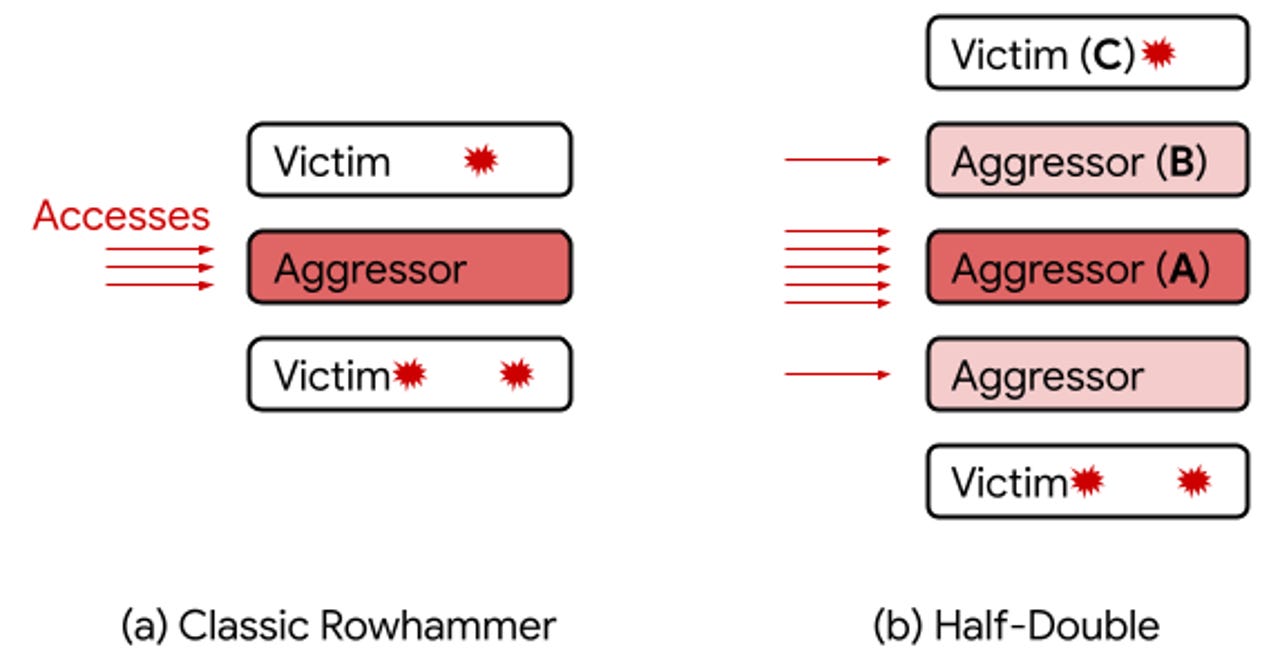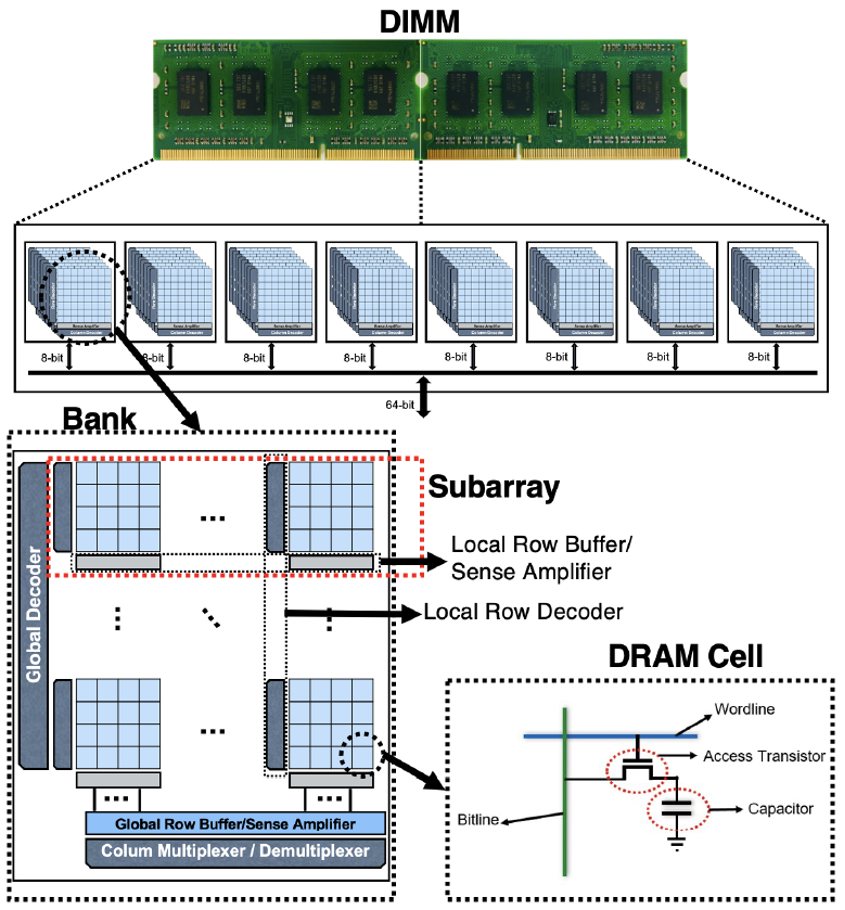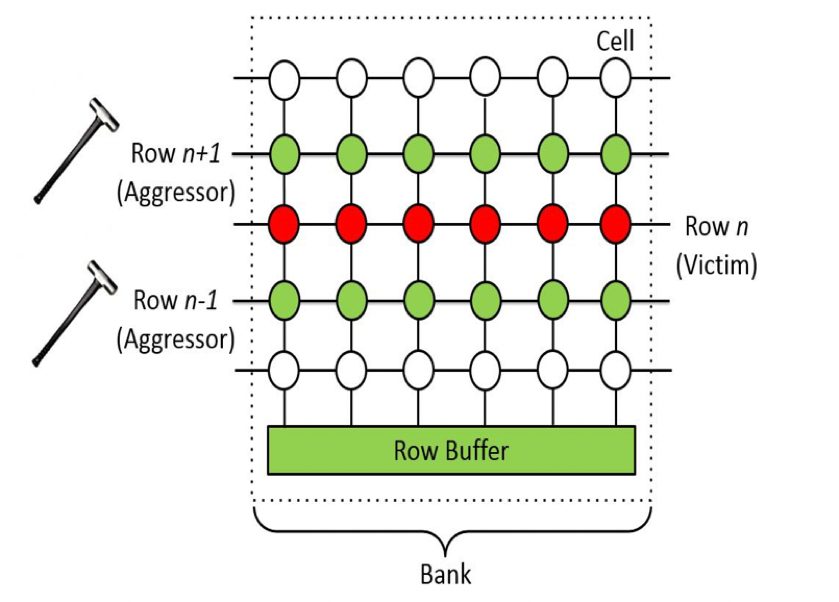
PC security facing another “heavy hammer”, Baidu Security discovers a new Rowhammer attack | by Baidu Security X-Lab | Baidu Security X-Lab | Medium

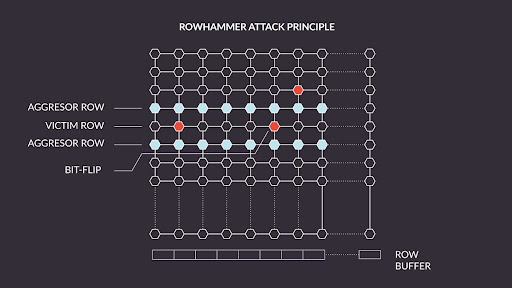
Row Hammering types: (a) Double-Sided Row Hammering (DSRH) with PUF... | Download Scientific Diagram
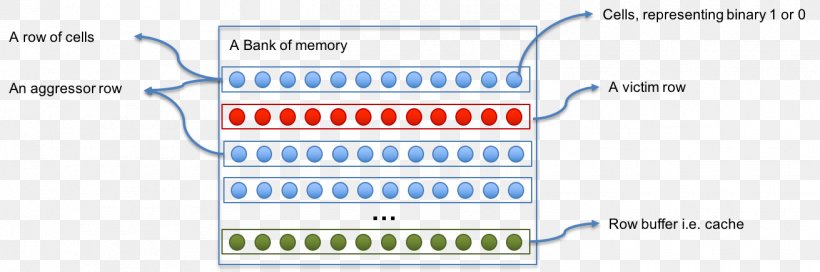
Row Hammer Exploit Android Computer Security Computer Software, PNG, 1311x435px, Row Hammer, Android, Area, Bit, Brand
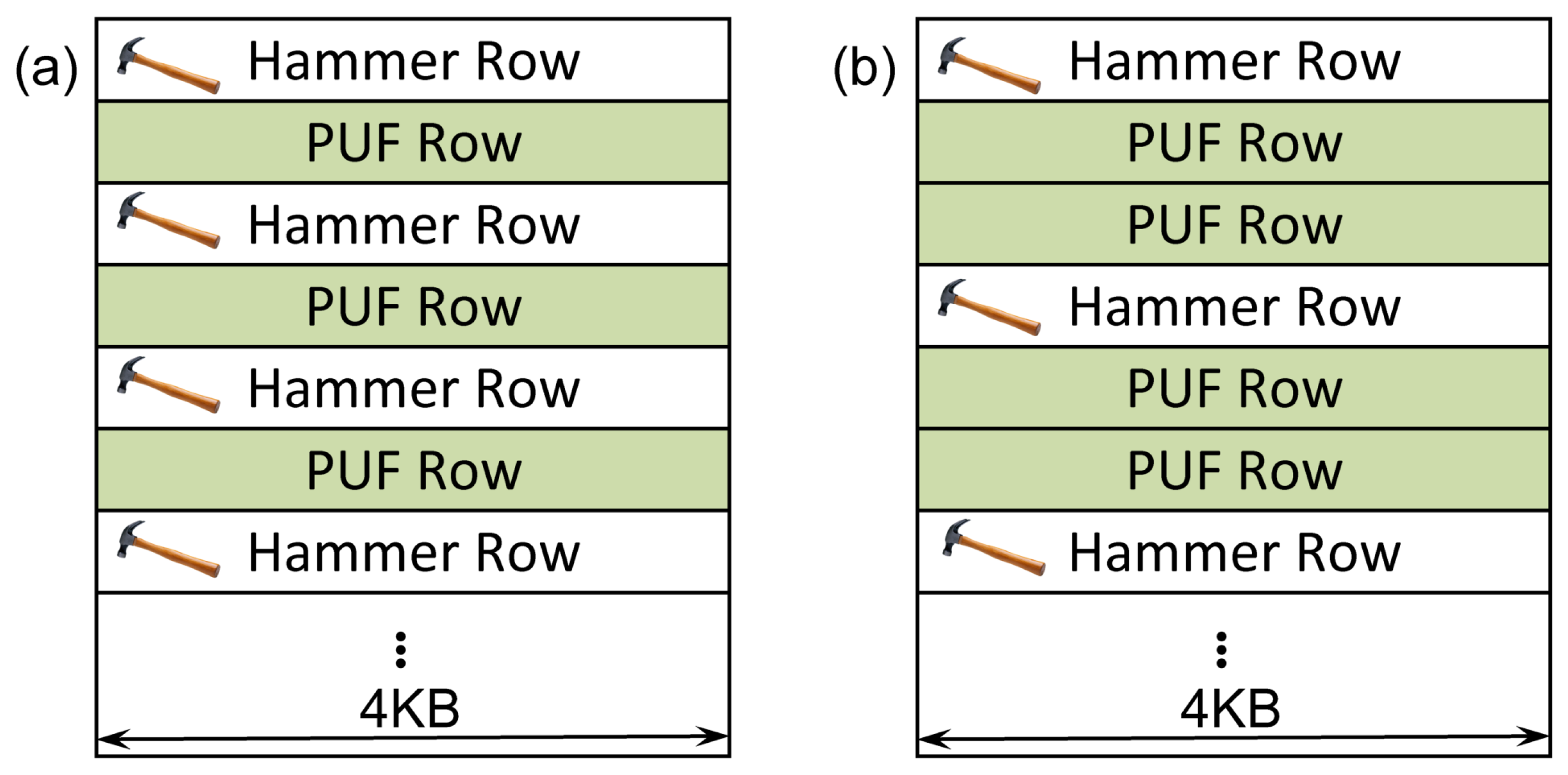
Cryptography | Free Full-Text | Intrinsic Run-Time Row Hammer PUFs: Leveraging the Row Hammer Effect for Run-Time Cryptography and Improved Security †
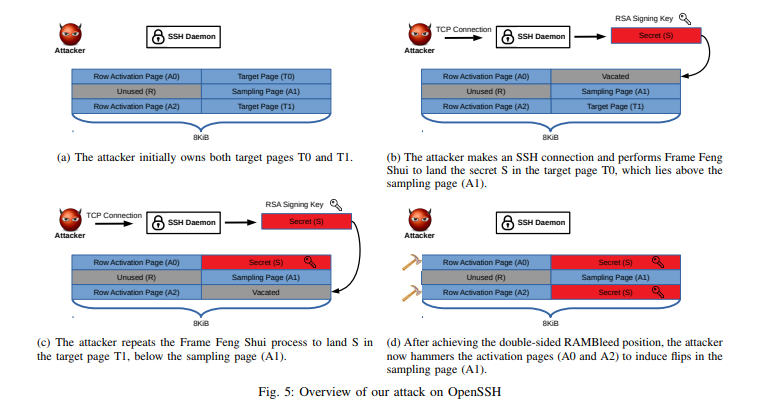
RAMBleed: A Rowhammer-based side-channel attack that reads memory bits without accessing them - Security Boulevard
![Security] How to exploit DRAM with Hammertime (Rowhammer🔨 attack step by step) | by Anna Kim | Medium Security] How to exploit DRAM with Hammertime (Rowhammer🔨 attack step by step) | by Anna Kim | Medium](https://miro.medium.com/max/1400/1*RiU39j2IHVBTFyXRewDEew.png)
Security] How to exploit DRAM with Hammertime (Rowhammer🔨 attack step by step) | by Anna Kim | Medium

Suppression of Row Hammer Effect by Doping Profile Modification in Saddle-Fin Array Devices for Sub-30-nm DRAM Technology | Semantic Scholar